What Is a Security Patch? Why It's Critical to Update Your Devices

Security patch updates represent your first line of defense against cybercriminals who exploit software flaws to steal data, install malware, or disrupt business operations. These small but mighty code fixes address vulnerabilities that hackers actively target, making them essential for protecting your digital life.
When you ignore that nagging update notification, you’re essentially leaving your front door unlocked in a dangerous neighborhood. Let’s explore why security patches matter so much and how you can protect yourself effectively.
What Do Security Patches Do?

A security patch is a targeted software update that fixes specific vulnerabilities in your operating system, applications, or firmware. Think of it as a digital bandage that closes security holes before criminals can exploit them.
Software vulnerabilities emerge when developers accidentally create weaknesses in their code. These flaws might allow unauthorized access, data theft, or system crashes. Once discovered, vendors release patches to seal these gaps.
Types of Security Updates
Different situations call for different patch types:
- Critical security patches address severe threats that need immediate attention
- Routine security updates fix less urgent but still important vulnerabilities
- Zero-day patches respond to actively exploited threats
- Cumulative updates bundle multiple fixes together
The EternalBlue exploit perfectly illustrates why patches matter. This NSA-developed tool, leaked by the Shadow Brokers, exploited a Microsoft SMB vulnerability (CVE-2017-0144). Microsoft had already released a patch, but organizations that delayed installation became victims of the WannaCry and NotPetya attacks.
Understanding the Critical Importance of Security Patching

The importance of patching becomes crystal clear when you examine real-world consequences. Cybercrime damages reached $10.5 trillion globally in 2022, with unpatched systems serving as primary attack vectors.
Unpatched systems create multiple risks:
Financial Impact: Data breaches cost companies an average of $4.45 million per incident. The Equifax breach, caused by an unpatched Apache Struts vulnerability, resulted in $1.4 billion in costs.
Operational Disruption: WannaCry ransomware infected over 300,000 computers across 150 countries, shutting down hospitals, railways, and government services. All because organizations hadn’t applied a Microsoft security patch released months earlier.
Compliance Violations: Regulations like GDPR, HIPAA, and PCI DSS require timely patch installation. Non-compliance triggers hefty fines and legal consequences.
Case Studies That Changed Everything
Target Corporation learned this lesson expensively. Hackers exploited an unpatched HVAC system to access their network, stealing 40 million credit card numbers. The breach cost Target $202 million and damaged their reputation permanently.
Conversely, organizations with robust patch management programs avoided these disasters. They implemented systematic approaches to vulnerability remediation and emerged stronger.
Patch Management Best Practices for Maximum Protection
Effective patch management best practices require systematic approaches rather than reactive responses. Here’s how successful organizations protect themselves:
Create a Comprehensive IT Asset Inventory
You can’t protect what you don’t know exists. IT asset inventory forms the foundation of effective patch deployment strategies.
Start by cataloging every device, application, and system in your environment. Include:
- Operating system patching requirements for each device
- Software versions and update schedules
- Critical systems that need priority attention
- Shadow IT assets that might escape notice
Modern discovery tools automate this process, scanning networks to identify devices and software automatically. This ensures your inventory stays current as your infrastructure evolves.
Determine Risk Levels Using Data-Driven Assessment
Not all vulnerabilities deserve equal attention. Risk-based patching helps you prioritize efforts where they matter most.
CVEs (Common Vulnerabilities and Exposures) provide standardized vulnerability ratings. The Common Vulnerability Scoring System (CVSS) scores range from 0.0 to 10.0, with higher numbers indicating greater severity.
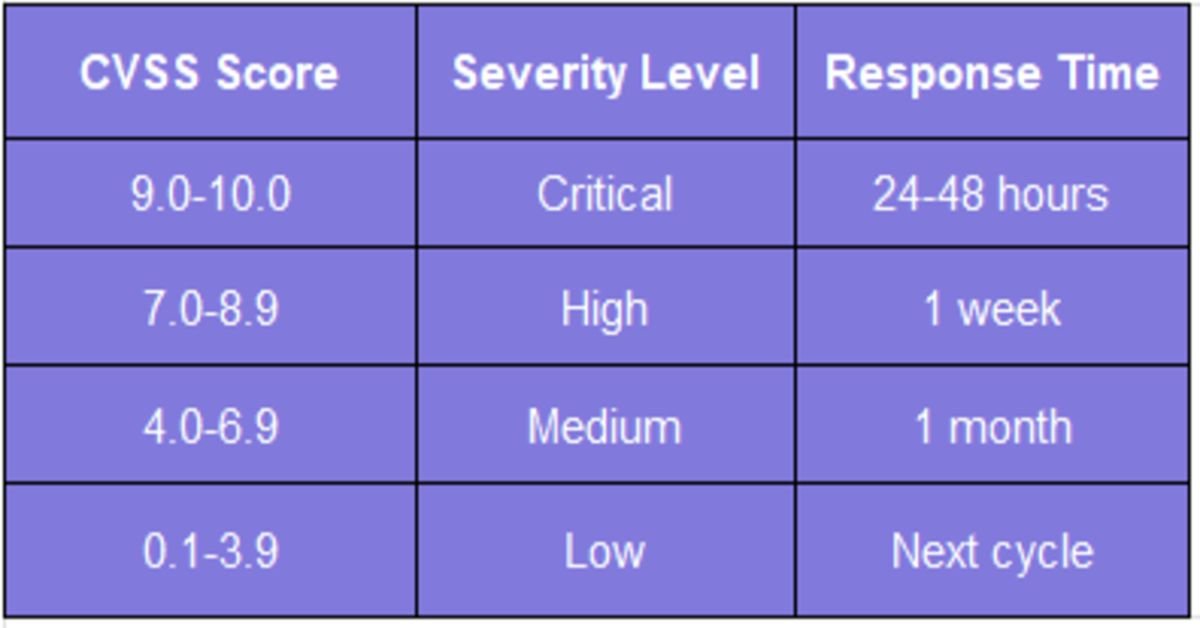
Consider business impact alongside technical severity. A medium-severity vulnerability affecting your revenue-generating systems may warrant faster attention than a critical flaw in rarely used software.
Test Patches in Controlled Environments Before Deployment
Patch testing prevents the cure from becoming worse than the disease. Even well-intentioned updates can break critical functionality or cause system instability.
Establish staging environments that mirror your production systems. Test patches thoroughly before widespread deployment. This includes:
- Functionality verification across all affected systems
- Performance impact assessment
- Compatibility testing with existing software
- User acceptance validation
Develop robust rollback procedures. Sometimes patches cause unexpected problems that require immediate reversal. Having a tested rollback plan minimizes downtime and frustration.
Consolidate Your Software Tools
Managing security updates becomes exponentially harder with fragmented tools. Unified patch management platforms streamline operations and reduce complexity.
Modern solutions provide centralized visibility across diverse environments. They automate routine tasks while maintaining human oversight for critical decisions. This consolidation reduces costs while improving security outcomes.
ServiceNow and similar platforms demonstrate how integration improves efficiency. Rather than juggling multiple dashboards and processes, administrators work from single interfaces that coordinate complex operations seamlessly.
Monitor Vendor Patch Announcements
Staying informed about vendor patch announcements ensures you never miss critical updates. Cyber threat mitigation requires proactive monitoring rather than reactive responses.
Subscribe to vendor security bulletins and automated alert systems. Major vendors like Microsoft, Apple, and Adobe publish regular patch notification schedules, making planning easier.
Join information sharing communities where security professionals discuss emerging threats. These collaborative environments provide early warnings about actively exploited vulnerabilities.
When to Seek Professional Assistance
Honest assessment of internal capabilities determines whether you need external help. Patch management complexity increases with organizational size and system diversity.
Consider professional assistance when:
- Your team lacks specialized security expertise
- Compliance requirements exceed internal capabilities
- Critical systems require 24/7 monitoring
- Budget constraints limit internal hiring
Managed Security Service Providers offer comprehensive vulnerability management services. They combine human expertise with advanced tools to deliver enterprise-grade protection at predictable costs.
Hybrid approaches work well for many organizations. Internal teams handle routine operations while external experts provide specialized support for complex challenges.
READ MORE ABOUT: Common Vulnerability Scoring System (CVSS)
Frequently Asked Questions
How often should I install security patches?
Install critical security patches within 24-48 hours of release. Regular updates can follow monthly schedules, but severity determines urgency. Cybersecurity incidents often exploit recently disclosed vulnerabilities, making speed essential.
What happens if a patch breaks my system?
Proper patch testing minimizes this risk, but problems occasionally occur. Maintain current backups and tested rollback procedures. Most vendors provide hotfixes and service packs to address patch-related issues quickly.
Should I enable automatic updates?
Automatic updates work well for home users and non-critical systems. Enterprise environments need more control over patch rollout strategy timing. Consider automatic installation for operating system patching while maintaining manual control over business-critical applications.